< Back to insights
Published 22. Mar. 2023
Microsoft Europe CSA: AI & Humans Must Evolve Together in Cybersecurity
The digital evolution brought along automation which enabled transformations of economies and businesses on a large scale. What does the rise of artificial intelligence tools and machine learning in the digital landscape mean for cybersecurity and how can humans evolve together alongside these technologies?
We caught up with Sarah Armstrong Smith, Microsoft’s European Chief Security Advisor about the impact of AI on cybersecurity and what the future of cybersecurity could look like.
1. Digital Acceleration Brings Evolved Threats
It’s estimated in the next five years that over half of the world’s data will live in the cloud. With that comes huge computational power that is available on demand and at scale, giving us the agility and flexibility to innovate.
A clear effect of this is the accelerated development and use of smart technology in recent years. For example, more companies are investing in digital twins which enables them to try different things and run diagnostics without having to do it in a physical environment.
However, this comes with concerns about security, particularly in high-tech areas that deal with intellectual property and other sensitive data.
The global spending on cybersecurity is estimated to grow to about 1 trillion in just a few years.
What does this mean for security? Multiple factors must be considered to ensure privacy, security, and compliance with regulations. Beyond that, there’s also the defensive side of anticipating and managing evolving threats. Not only do we need to obtain information, but we also need to know how to act on it efficiently in real-time. This is where AI comes into play.
2. Security is in Transformation
The early discourse on AI verged on alarmist with warnings that the technology would eradicate jobs and leave millions of workers out of an income. In fact, the World Economic Forum projected that AI and automation would displace over 5 million jobs by 2020. However, the open market now has about 6 million unfilled cybersecurity jobs alone. In fact, there is a huge demand for talent in robotics, machine learning, IoT, big data, and AI.
The mass migration of businesses to the cloud at different levels of maturity has shifted expectations on the type of connectivity provided, devices used, and trustworthiness of those devices. Most enterprises are running a hybrid business model due to challenges with the legacy estate. This complicates cyber security efforts. Security leaders are compelled to understand the integration between the IT, IoT and cloud environments in order to ensure a connected ecosystem that is smart, reliable and safe.
With all that combined, there is an increased attack surface and multiple blind spots. Particularly, organizations are still deeply fragmented when it comes to their approaches. At the same time, cyberattacks are rising exponentially.
Moreover, attackers are becoming more sophisticated. They can move very quickly and outmaneuver security operations and technologies of even larger organizations because they are not constrained by regulatory requirements. Attackers are also investing heavily in automation and scripting.
Every time attackers bring out new malware or new attacks, we learn those, we counteract them, we have detections, we’re automatically blocking the malware, and different attempts that they’re trying. However, we know that resources are at a premium and we can’t just add and throw more money at it.
“We have to think of ways in which we can increase the attacker’s cost and reduce our cost with our ability to act and respond as quickly as possible.”
3. What Can CISOs Do?
A. Prevention of threats
The first imperative is we need to prevent as many threats as possible with automation. We have to detect, we have to respond quickly and we have to continually learn. As much as the attackers are learning our defenses, they’re learning about the technologies that we have, they’re learning how to counteract that. When they’re counteracting that, the whole cycle starts again. We’re seeing this perpetual cycle of prevention, detection and response.
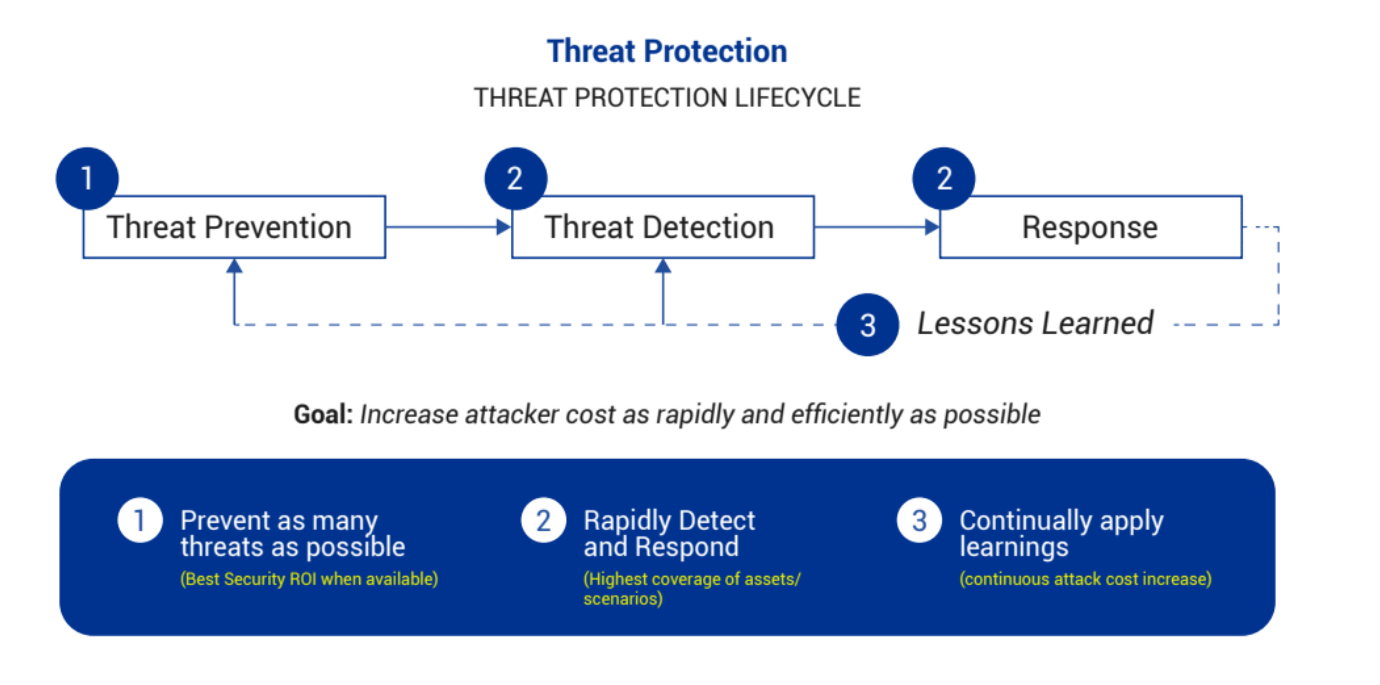
B. Understand human attacker decision cycle
With human operator attacks, particularly ransomware operators and nation-state actors, part of their attack profile is really their ability to observe. They have to sit, watch and learn about your environment.
We know that attackers understand IT infrastructure very well. What they don’t understand is how you specifically deployed technologies in your environment or other technologies you are utilizing. They have to learn and orient across your environment, and potentially keep elevating privilege. They have to get access to different parts of the infrastructure to learn what to do and what attack is going to work best in this environment.
This is the kind of cycle we’re really looking at when it comes to that human attacker decision cycle. From a security operations perspective, our job is really to understand this cycle. Irrespective of the fact that they probably have been in that network for weeks or months, it’s really at the point where they have triggered some kind of action that we respond.
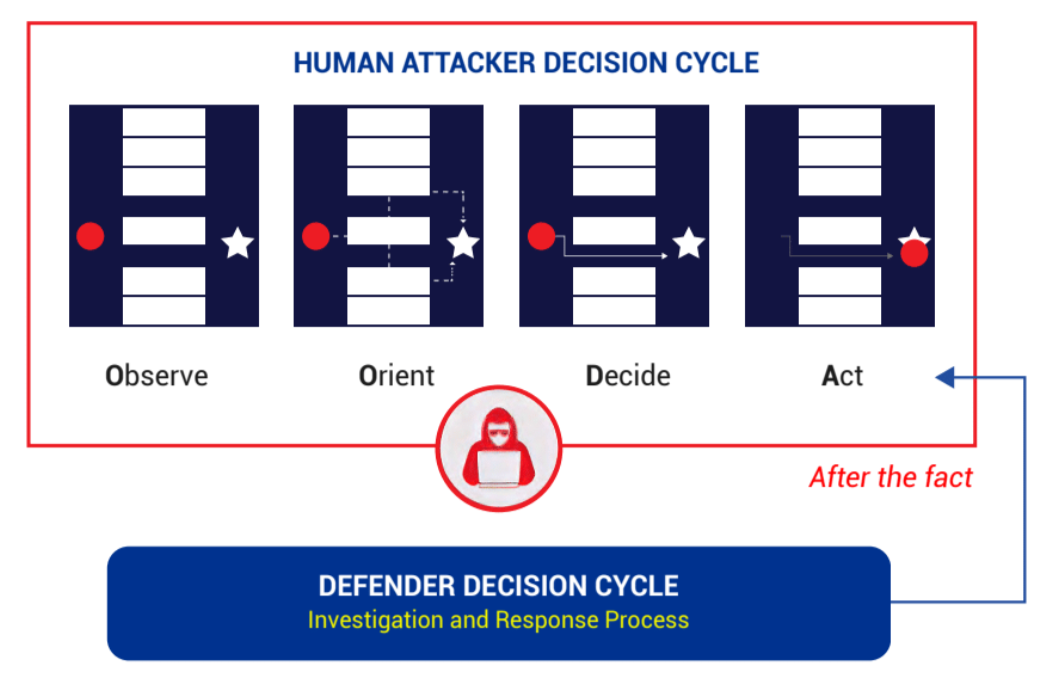
We need to get better. We need to be proactive and preempt. We need to understand how the attacker is operating, understand this cycle, and get into the mind of the attacker for us to be able to make some decisions.
Where this comes to is our ability to defend and act quicker across that entire cycle, meaning we need to maximize the visibility of our network. We need diversity of threat intelligence, and we need that from different sources. Importantly, we need that real-time information.
C. Automation + humans in threat detection and response
The other thing that we need to do is reduce the number of manual steps or potential errors that may occur. Part of this is about the ability to automate that detection and response. From security operations, we don’t want to be pivoting across different technologies because that decreases the time that we have to act. It potentially means there are going to be more errors because we’ve got conflicting or duplication of information.
With that, we have to maximize human impact. We’ve got to get this information and intelligence in front of our humans because it’s humans that understand the context, it’s humans that understand the business risk, and it’s humans that understand consequences.
“We’ve got to get the human and automation layer right. This is about continuous learning.“
We need automation, we need those evasion techniques. However, we also can’t stop every single attack now because attackers are evolving at pace. Instead, we have to assume a compromise mindset.
What the Future Looks Like in AI & Cybersecurity?
In terms of the future, we’re going to see more use of virtual reality and mixed reality. We’ve already talked about how AI and automation are going to really shift our ability to get deep insight. Looking at how attacks are evolving, it’s estimated that we’re going to see an IoT botnet, which is probably going to be able to launch one of the biggest DDoS attacks that we’ve ever seen. We will probably also see a cyber attack of such magnitude that one of the countries will be forced to carry out a physical attack against the nation state that targeted them.
We will also start to see not just digital buildings, but digital cities which increases the attack surface. We’re going to see the proliferation of cyber-attacks at scale, infiltrating the IT the IoT, and OT simultaneously. That’s going to drive the need for regulatory control and human oversight with regard to how these AI and ML machines are working, the decisions that they’re making, and the ability to cause a disruption at that scale.
AI & Humans Must Evolve Together
We’ve got to use AI and ML, but we have to also understand the behaviors of those humans and overlay these technologies with human expertise. We then have to increase our speed and quality of detection and response to be dynamic in real-time to threats as it happens. We have to keep speeding up the response with our orchestration and automation.
As we’re moving farther into that mixed augmented reality, the real value for security operators is to actually visualize that infrastructure. When they can see the attackers coming through the network, they can see them literally moving across the estate, it means they can start to take action at scale.
“Ultimately, we are not going to take any humans out of the equation. In fact, the reality is we’re going to have more augmentation between the AI and the human combined.“
