Facial recognition addresses the core problem of personal identification which has broad applications within (and beyond) the events industry. Couple it with adjacent technologies such as emotion recognition or human posture recognition and the possibilities are limitless. You gain full control.
This is more than a cool technology that people will start using sometime in the future. Facial recognition adds clear value such as improved security and better user experience along with unmatched analytics and insights. It is already used to tag photos on social media, unlock and pay with cell phones, and go through border security. Since people are getting accustomed to the technology, facial recognition is becoming an expected service rather than a nice to have feature. 2018 is the year innovative events are embracing facial recognition. ##abovethefold##
Every powerful technology comes with great responsibility. Respecting people’s privacy and handling metadata in a transparent and prudent manner is a necessity. Every party that has access to this type of information should be trustworthy and held accountable to the highest standards.
What is Facial Recognition?


Humans are great at identifying people they know well. However, our ability to remember and distinguish individuals diminishes when the number of people grows to more than a few dozens.
Since it is not always efficient to rely on people for this task, we have come up with alternative forms of authentication. In particular, there are three forms of authentication that rely on: (i) something that the user has, (ii) something that the user knows, and (iii) who the user is.
Examples of physical tokens in everyday life include home and car keys, credit cards, passports, and driver’s licenses. Equivalent examples within an event would include printed tickets, badges, wristbands, and mobile phones.
When it comes to examples of privileged information, everyone is familiar with usernames, passwords, and security questions. In the context of an event, there are a lot of check-in applications that rely on name/email searches and scanning QR codes.
The use of physical tokens and privileged information have become integral parts of an event lifetime. They are used to check-in people, restrict access, personalize the experience, measure attendance, extract analytics, and perform lead retrieval.
Facial recognition belongs in the third form of authentication along with other biometrics approaches. It is a software which can identify a person from a database of faces without requiring a physical token nor the user to provide any privileged information. Technological advancements have increased accuracy and reduced cost drastically. Therefore, we see increased adoption in other industries (e.g., airports, social media, and cell phones).


7 Ways Facial Recognition Can Improve Your Event
The ability to identify people in a scalable, non-intrusive manner has substantial benefits and numerous use cases. In other industries facial recognition has been used for access control, surveillance, time attendance, personalized marketing, enhancing the user experience, and extracting analytics. The possibilities within the events industry are just as exciting.

1. Check-In
Regardless of the event type, one simply cannot overstate the importance of a smooth and efficient check-in process. People waiting in line makes a bad impression and kills the mood. Why do we see long lines at events? Several factors make the process inefficient. The attendees are not always good at following the instructions displayed on the terminal, they cannot find their ticket, it takes them a while to retrieve the QR code on their phone, or they simply need time to type in their email address. In many cases, we see people coming to an event with their hands full meaning that they must place their belongings down before they can initiate the check-in process.
This leaves the event planner with two options: (i) try to work around the problem, or (ii) address the bottleneck which is causing the problem at hand.
Some options in the first category include drastically increasing the number of check-in stations (which in turn increases costs and overheads) or adding check-in stations into airports and hotels which can be a logistics nightmare.
Facial recognition falls into the second category of addressing the root cause of the problem by eradicating the need for user actions. Depending on your preference, you may want to implement a self-service or a hosted check-in mode. In either case, the premise is the same. When an attendee approaches the check-in station they will be instantly identified without them having to take any action. That is all.
The best part is that you do not need to purchase expensive hardware because any device with a camera works. This includes virtually all laptops, tablets, and smartphones. In addition to making the check-in process more efficient and thus reducing costs, face recognition has been proven to increase user engagement and attendee satisfaction. It is an excellent way to promote the innovative nature of your brand and impress attendees.


2. ID Check
It is more important than ever to increase security at events. To this end, we see more and more checks that rely on different forms of identification documents (IDs) such as driver’s licenses and passports. In certain regions of the world, checking the ID of people walking into the venue is required by law enforcement. In other cases, the ID check is enforced by regulations such as restrictions on liquor sales.
Even though checking the ID of the attendees entering the venue is a step in the right direction, most of the existing implementations have limitations. Attendees are asked to present their ID and an untrained host is taking a quick look before giving it back. This is not enough. Doing a proper ID check, on the other hand, is time-consuming. One would have to check the issue and expiration dates, scan the code and make sure it matches the ID unique number, check whether the picture matches the person presenting the document, and so forth.
There is a faster and more secure way to perform this task. In particular, attendees can be requested to take a picture of their ID along with a selfie when they register online. A facial recognition algorithm will ensure that it is a real picture (liveness/spoof detection) and that the two faces match; other computer vision algorithms will perform the rest of the checks in real-time. We see this approach being used widely in other applications such as the banking and hospitality industries (e.g., Airbnb).
If one would like to have more control over the ID check process, they could opt for an on-site implementation. Specifically, the use of specialized hardware (i.e., scanners) can facilitate a deeper analysis of the IDs but it typically increases the corresponding investment required.
In either case, the use of computer vision and face recognition can significantly increase the security and efficiency of the ID check process. People are becoming increasingly familiar with online ID checks because they are asked to follow the same steps when using other services.


3. Watchlists
One of the most effective ways to increase security is by actively scanning people attempting to get into the venue and ensuring they have a clean record. As we mentioned, humans are great at remembering people they know well. However, our memory fails us when we are asked to identify a person from a large database of faces. Facial recognition makes this easier and more efficient than ever.
One can compile watchlists with ease these days by using publicly available records. Such examples include the most wanted criminals listed online. If the event host is aware of known troublemakers, it is possible to add them to the watchlist. Using regular cameras at points of interest is all that is needed. The system will continuously scan the database and alert you if there is a person that needs to be checked. One could combine this with the check-in process to maximize efficiency. When an attendee approaches the check-in station, the system can search the list of registered attendees and the watchlists. That’s killing two birds with one stone.
Watchlists are most frequently associated with people that must be kept out of the venue. We tend to refer to them as blacklists. However, in many cases, it makes sense to compile whitelists as well. For example, as the event host, you might want to treat very important persons (VIPs) with special care. If you use whitelists, each time a VIP arrives at the registration area you will be instantly notified and quickly able to cater to their needs.
4. Session Tracking
According to the State of the Event Industry, 2018 Survey by EventMB, education and networking are the top two priorities for corporate event attendees. Hence, event hosts spend a significant amount of time recruiting speakers, curating the content of their shows, and organizing sessions that cover different aspects of the event theme. In addition, conferences with a deep educational focus often assign credits and accreditation to participants who attend specific sessions.
Event planners have limited resources and they need to allocate them accordingly. Therefore, it is important to efficiently and effectively track the participation of different sessions. Knowing which sessions are the most successful can be used to promote next year’s event by doubling down on them while removing sessions which did not attract a crowd.
In addition, having a good grasp of the average participation rate can help book rooms of the appropriate size to prevent half-empty rooms (which do not look good) and increase budget optimization. More importantly, one can uncover patterns about the combination of sessions that are the most attractive to specific types of attendees using attendance, instead of enrollment, data. Bundling these sessions can assist in organizing next year’s sessions in a data-informed manner which can result in increased ticket sales, respective ticket price adjustments, and thus increased revenue overall.
Face recognition is a good fit for this use case because it requires minimal setup and extracts analytics in a non-intrusive manner. Depending on different technical factors, session tracking with face recognition can be as simple as putting a tablet or cell phone on a stand near the entrance of each room. The camera will automatically capture the video stream and send it to the cloud for processing. There is no need for special hardware and expensive installation costs.
Unlike badges and passes, which can be passed between people, faces are known to be non-transferable. This is particularly important for events which have a strict learning credit system or any event planners that organize sessions with sensitive content or otherwise valuable information.
5. Heatmaps
Organizing an event with multiple points of interest presents unique challenges and opportunities. For events that fit this profile, it is important to identify and address potential bottlenecks by allocating resources accordingly in real time.
A common example includes stadiums and festivals with long lines at different gates around the site. Exhibitions and conferences with a tradeshow floor are also good examples. Getting the bird’s-eye view is vital in coordinating the on-site support staff effectively. In addition to assessing and addressing challenges, one can extract meaningful statistics that can directly improve the bottom line. A trade show organizer can understand the crowd flow in a more effective way. This knowledge can be used to follow up with the exhibitors and offer them insights which can help them compute their conversion rates. The organizer can emphasize the value they received by attending the trade show to increase renewals.
Furthermore, the same information can be used to adjust prices for different booths at next year’s show, thus increasing revenue. In addition to closing better sales, heat maps can be used to shorten the decision cycle. There is nothing more convincing than sharing with potential exhibitors hard data about the number of people that are expected to pass through and visit their booth. Cite their competitor’s performance at a past show and you have a perfect pitch to sell out fast.
Face recognition can be a great way to compute and draw heatmaps. Tracking the number of faces visible by the camera across the different event locations is straightforward. It does not require special hardware and it is easy to install and configure. Depending on the level of investment, the information can be as high level as how many people on average stood and passed by a certain point of interest or as fine-grained as extracting insights by group type and knowing each attendee’s journey.


6. Convenience & Personalization
According to State of the Event Industry 2018 Survey by EventMB, the vast majority of event professionals use the attendee satisfaction and user experience as the core metrics to measure the return on investment (ROI). Offering attendees easy access to information and making them feel important are good ways of improving their experience. And there are many opportunities to accomplish this throughout an event, in addition to all the other use cases mentioned above.
One can use screens (equipped with a camera) around the venue that identify attendees and display personalized information ranging from where food is being served to which is the next session they should attend. Likewise, the information desk personnel could be equipped with similar capabilities. Being able to identify a person while they are walking towards the desk allows them to personally greet them and anticipate their needs. Along the same line, one could combine face recognition with chatbots to offer the most efficient and personalized customer service. There is a myriad of interactive applications that could be developed. It is up to your imagination.
Finally, using face recognition to enable cashless payments improves the user experience and increases revenue. This can be applied to a number of different occasions such as addressing outstanding balance during on-site registration and purchasing food and beverages at the bar.
7. Lead Retrieval
The core function of exhibitions and trade shows is to facilitate networking and spur new business opportunities for the participants joining the event. As the attendee, you want to receive written communications only from service providers you are genuinely interested in. As an exhibitor, you want to prioritize and focus on leads which are a good fit. In addition, you want to have access to statistics that help you maximize the return on investment from attending the show. This is one of the use cases where face recognition can make a big difference.
It is common to allow attendees to book appointments in advance of the event with exhibitors they would like to visit. During the online booking process, exhibitors can ask questions to identify the needs and likes of the person making the appointment. This presents a unique opportunity to learn more about the attendee and, with the help of face recognition, greet them by name when they visit your booth.
Anticipating people’s needs means that there is no need for the attendees to reiterate their pain points each time. Everyone can focus on topics which are of mutual interest and value. The exhibitor could go one step further and offer a VIP experience by having their favorite beverage ready. A more efficient and pleasant process benefits everyone; the event planner, attendees, and exhibitors.
Improving the attendee experience puts them in the right mindset to make a purchase decision. However, face recognition can empower exhibitors beyond this. Currently, exhibitors have to manually scan each person’s badge and enter all the relevant information into a lead retrieval application to summarize the discussion. With face recognition, it is possible to automatically keep track of how many and which people visited the booth. The lead generation and conversion statistics are vital in the sales process.
In addition, this technology allows you to keep track of how long attendees stayed at the booth and how they were feeling. Analyzing their sentiments combined with the information collected before/during the show enables lead management like never before.
At the end of each day, the exhibitors will receive a full report. The leads will be automatically scored by their likelihood to make a purchase decision so that the team can focus on the best targets and following up promptly. Face recognition combined with audiovisual sentiment analysis will have a dramatic impact on leads retrieval.


5 Myths and Misconceptions About Facial Recognition
Disruptive technologies are usually frowned upon at first. However, people are gradually convinced about the benefits and when they feel it is safe they become strong advocates. In the process of accelerating the adoption rate, it is important to highlight the benefits but also address any concerns and misconceptions your event attendees may have. Some of these myths are more founded than others. Here we will elaborate on a few key concerns and how to address them.


1. People Think Facial Recognition is Creepy
The correct thing to say is that some people think it is creepy. Real-world deployments by Zenus and its registration partners show that the majority of the attendees are willing to use facial recognition. That is, the first time an event planner will introduce the option they can expect 50-60% of the people to upload their photo. We see attendees talking to their friends and colleagues about how fast and easy the check-in process was so we expect the opt-in rate to grow for repeat events.
The great thing about facial recognition is that not everyone must opt-in. Instead, it works in conjunction with name search and barcode scanning. The same check-in station can simultaneously allow attendees to use any of these three ways to get their badge. If you have enrolled in face recognition you will simply go through faster. If you have not then you will need to use the traditional ways.
It is worth noting that a participation rate of 20-40% is enough to make a difference to the on-site registration process. Speeding up the process for this portion of the registered attendees can address the bottleneck. This has been validated by studies on traffic jams and we have seen it with our eyes at events we have supported.
Finally, good communication can reassure attendees that might not feel comfortable. We have never had an attendee feeling their privacy was not respected because the event planners working with us were proactive and not reactive. When calling people to participate, the event planner can and should explain this is an optional service. Moreover, they should collect explicit consent during the image collection process using a checkbox and explain what is happening with the data. As long as there are sufficient security measures enforced there is not much to worry about.
2. Collecting the Images is Hard
There are plenty of online registration companies which already allow attendees to upload their headshot or take a selfie. Most devices such as laptops, tablets, and cell phones have a front-facing camera. If necessary, one could opt to use their social media profile picture. Hence, collecting the images is not as hard as people might think.
The catch is that most registration companies do not assess the image quality, resulting in a poor images being collected. Nevertheless, this is something that can be easily mitigated by working with the right vendor. Registration companies working with Zenus have already successfully mitigated this risk.
Requiring ID checks is a good way to push up the adoption rate and collect images from attendees during the online registration process. People understand the need for added security and that performing the check online is easier. Alternatively, one could enable on-site image collection to ensure that all badges include the person’s face on them. This can drive up the opt-in rate to face recognition and facilitate other use cases. Overall, the widespread adoption of devices with a camera makes the image collection process easy; it is a simple logistics process that can be streamlined with little effort.
3. Facial Recognition Technology is Expensive
Some technologies are expensive, especially the ones that require specialized hardware, customizations, and on-site support. However, software-based applications tend to be more affordable. Luckily, face recognition falls into this category. Unless the event planner has excessive requirements, the associated investment is just a few cents per attendee expected to register.
Face recognition is a great investment. In most cases, the associated cost savings alone are enough to make it pay for itself. For example, it can increase the check-in speed by a factor of 2-10x. As a result, you can check-in the same amount of attendees using fewer check-in stations, less support staff, and a smaller registration area, which are all great ways to improve the bottom line for your event.
As with everything, there is always a trade-off between quality and cost. Therefore, one should be careful about the vendor they choose to use in order to reap the benefits. Event planners have more power than they think. For more on this, see how to choose the right technology provider.
4. There are High Requirements for Facial Recognition
This could not be further from the truth. Uploading one good picture during the online registration will suffice for most applications. Using any device with a decent camera such as a laptop, tablet, or a cell phone is enough to recognize a person during check-in. The video is streamed to the cloud and processed there so the device computation requirements are minimal. Depending on your flexibility and expectations, the required internet bandwidth can be less than 0.5 Mbps (upload) for each device powered by face recognition.
For full blown implementations and stringent requirements, a little more effort might be required. On these occasions, on-site support could be a good idea. However, for the vast majority of the cases and in comparison with other high-technology alternatives face recognition is probably the most user-friendly and easy to use option. You simply point and recognize. Simple. Remote support is enough for most of the events and it will rarely be needed.
5. Facial Recognition Does Not Work as well as Advertised
Even though this is related to the previous point about choosing the right vendor and the tradeoff between quality and cost, it is nuanced enough to treat it separately. Some companies might overpromise on what they can deliver. This is particularly true if these companies do not have significant domain expertise and previous real-world experience. Things work well in the office, when offering demos, and in small-scale applications. This may mislead both the event planner and the technology provider itself.
Hence, it is vital to work with the right biometrics vendor so that you will get a clear picture of what is feasible and what is not given the requirements at hand. For big projects, it is important to take the time and schedule a couple of calls which include all stakeholders. The event planner should make an effort to communicate the objectives and requirements, and the vendors at hand should explain what is feasible given the time and budget constraints. Managing expectations is crucial for all projects.
In summary, facial recognition has limitations but it can work as expected as long as you choose the right provider.
A Deeper Dive into Privacy and Accuracy
Even though facial recognition is intuitive at its core, certain elements that surround this technology are nuanced. Below we summarize a few aspects which can offer a deeper understanding of how the technology works. After getting equipped with this knowledge, we elaborate on concerns about privacy and data transfer.
1. Facial Recognition: How it Works
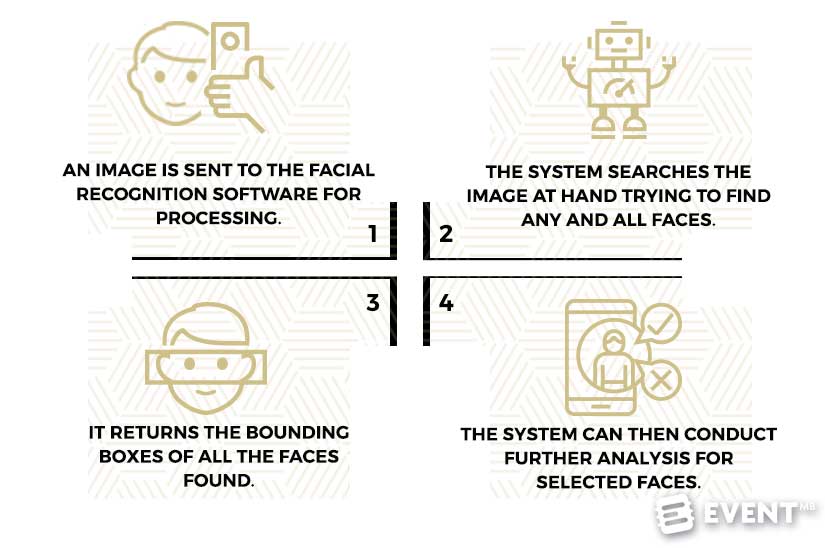

Let us start with the basics.
- An image (or frame from a video sequence) is sent to the facial recognition software for processing which typically resides in the cloud
- The system searches the image at hand trying to find any and all faces
- Once this step is done, it will return the bounding boxes of all the faces found
- Depending on the settings, the system can then conduct further analysis for selected faces
This analysis typically processes the region within the corresponding bounding box and extracts different types of face measurements. Depending on the problem at hand, the corresponding measurements can be used to predict the facial expression, personal identity, and so forth. Each process takes just a few milliseconds and it is typically faster than the blink of the eye.
Within the events space, the registration company and event planner are typically the data controllers. Before the event, they send images to the biometrics service provider. Each time an image is sent to the biometrics system a response content is returned. For example, if an attendee uploads a poor image during the online registration process, the system can provide real-time feedback that a better image must be provided.
If the process has been implemented correctly, the images are anonymized by the registration platform before they are sent to the biometrics service provider. Moreover, all the data transmission will happen through encrypted channels. The images will be processed by the biometrics service provider and instantly discarded without ever being stored on the hard disk. What is stored typically includes the face measurements. If an attendee would like to opt-out at any given point, the request can be processed by the registration company and delete any and all records in the biometrics server.
A frequent question is whether it would be possible to reconstruct the original image using the face measurements. The answer is yes and no depending on the safeguards employed by the biometrics service provider.
2. Authentication vs Identification
Assuming that the database with the face measurements has been populated, there are two types of tasks that face recognition can address: authentication and identification.
The first one is typically used in two-factor authentication processes where the person of interest makes a claim about their identity and then provides their biometrics measurements. The biometrics system will then compare the measurements just obtained to the template stored in the database for the claimed identity and make a decision. This is what we are usually referring to as one-to-one (1:1) comparisons.
The nice thing about authentication tasks is that the accuracy is relatively high and the size of the database does not impact performance. On the downside, a person must make a claim about their identity first which defeats the purpose. Moreover, most biometrics companies report the accuracy obtained when comparing “easy pairs” and not hard cases where people might look alike.
The identification task is more useful for real-world applications. Each time a picture or frame from a video is sent to the biometric server, the face detector finds all faces. Typically, the largest face (i.e., the person standing close to the camera) is processed to extract the face measurements. The biometric system will then search the database and retrieve the most likely match based on the measurements at hand. Depending on the settings, the system can either return a response content saying that this is the most likely match or it can try to make a decision.
Simply saying that this is the most similar face is an easier problem. Assuming that the person standing in front of the camera has enrolled, the chances of finding the correct match are pretty high. This is what we typically refer to as identification rate and it is a way to measure accuracy. When the database size increases, there are higher chances of having people who look alike and thus the identification rate decreases.
If the system settings require the biometric system to make the final determination (i.e., an automated decision), the problem becomes harder. To be precise, the larger the database the bigger the drop in accuracy. On this occasion, the system will either result in a high false positive rate (i.e., saying there is a match when there is not) or in a high false negative rate (i.e., rejecting a user who has been enrolled).
3. Privacy Regulations
There are several regulations that restrict the use of biometric data. For example, at the time of writing, the states of Texas, Illinois, and Washington have adopted biometrics regulations. Moreover, the European Union has passed the General Data Protection Regulation (GDPR), which has specific requirements in terms of sensitive data. Even though these regulations might make certain use cases hard to serve, they have a place because in principle they are protecting the privacy of end users. They are making every party involved aware that it is not right and acceptable to misuse people’s personal data. And in a way, they are bringing the facial recognition technology on the same (or similar) level with other tracking technologies such as RFID and Beacons.
Even though you should use a legal counsel for these matters, these are some steps that can help you reach compliance. When collecting people’s photos make sure to use a check-box to record the consent and explain clearly the way data is going to be used and for how long they will be kept. Hiding a few sentences into the terms of use is not acceptable, it must be a positive opt-in process. If the event is taking place in a country with strong restrictions, make sure to use signs indicating that the area is using face recognition and offer an alternative to the face recognition technology which is equally accessible.
In some regions, it is not okay to scan people’s face without their explicit permission. That is, placing a camera which is scanning everyone’s face and extracting their face geometry is not a good idea. Scanning all the faces in a picture is not a good idea either because there might be this one person who did not opt-in. It is not the process of enrolling their data that is usually prohibited. Instead, it is the process of calculating the face measurements without explicit permission that is not permitted.
4. Data Transfer
In addition to privacy regulations, one has to be aware of data transfer restrictions. This can actually be broken into two aspects; namely, data transmission and data transfer.
The wording “data transmission” is usually meant to describe the way data is being transferred between different systems; the way they are communicating. In particular, the golden standard is to use fully encrypted connections.
If you visit a website and the address starts with https://website.com this means that any communication between your device and the website will not be encrypted. Someone can easily steal and read all the content transmitted back and forth. Some browsers are going to mark these websites as not secure. A company with good security protocols will automatically divert all traffic to the https://website.com domain. Give it a try and you will be surprised by how many websites do not have a certificate to allow secure data transmission. Even some websites that do have a certificate, allow you to use the unencrypted version without automatically diverting traffic to the encrypted connection. The same can happen with the transmission of data between the attendees, online registration vendor, and biometrics service provider.
In addition to data transmission, one has to be wary about data transfer. Events typically draw international crowds and thus should be used extra carefully. As always, it is best to consult a legal counsel for these aspects.
If an event is taking place in Europe, it is usually a good idea if the vendors you are using are leveraging cloud servers in the same region and not outside the EU. Some online registration companies offer different options but not all providers do. In most cases, event planners are not presented with the option in the first place. However, under GDPR, they are still responsible for treating data properly because they are the data controllers and they are responsible for holding the vendors they use to the highest standards.


How To Choose the Right Facial Recognition Technology Provider
Choosing the right technology provider can be hard, whether you are an event planner or a registration company. Specifically, understanding how to evaluate the performance and value of a technology across different tasks requires deep subject matter knowledge. It is not enough to rely on public benchmarks because they are not comprehensive and they do not reflect the accuracy you can expect in the real world. Likewise, you cannot rely on demos or small-scale deployments. The good news is that there are ways to help you choose the right vendor with relative peace of mind. Here are the three main criteria to consider.


1. Domain Expertise
Several companies develop a generic solution (or simply resell open-source software) and expect this to work well across use cases and industries. Even if it works in the short term, this is something that will not last. There are two reasons for this.
First, designing and implementing a complete solution requires domain expertise in biometrics and events. Unless the registration provider and technology vendor work closely together and unless the biometrics company has developed a deep understanding of the needs/requirements across several events, the end product will not be scalable. There will be deficiencies at scale which will hurt all parties involved. Domain expertise is not transferable and it is vital that all stakeholders speak the same language.
Second, there will always be a need to develop new features that adjust to the market needs. For example, one might use face recognition for check-in and then decide to add online ID checks. And when this is done, the events industry might require speech recognition and sentiment analysis to improve leads retrieval applications. Unless the technology provider is committed to serving the events industry, the interests of the stakeholders will not align. This will require the event planner to either bring in more technology providers (which is not efficient at all) or switch to a technology provider that focuses on the events industry. Why not work with the right technology partner from the beginning?
2. Compliance
There are quite a few companies which allow registration companies to access their cloud-based services and create an integrated solution without ever signing anything. Everything is hidden in generic terms of use. As a result, there is no guarantee that the technology provider is compliant with privacy and data transfer regulations, there is no liability whatsoever on their part. If you are a registration vendor it is vital to execute a formal agreement with the technology provider and if you are an event planner it is equally important to ensure your registration vendor has such an agreement in place.
Using a technology provider that does not ask the registration vendor or the event planner to review and sign such a legal agreement is a red flag. In line with the previous point, a technology provider focusing on the events industry will have an agreement tailored to the use cases at hand. This provides clarity so that everyone is accountable for their part.
In business, one should always hope for the best and be prepared for the worst. You do not want to be unprepared. Hence, you must work with someone that has a high level of responsibility and professionalism.
Part of compliance includes respecting privacy and data transfer regulations. In addition to signing an agreement which details how the technology is treating data, you should ensure that the provider has a seamless way to allocate cloud resources in different regions around the world depending on where the event is taking place. Otherwise, you will be undertaking a significant risk and liability whether you are an event planner or a registration company.
The same applies if you would like to develop applications that track attendees throughout the venue. Since in many regions of the world you are not allowed to scan all the faces in frame, it is important to work with an experienced provider that knows how to address and overcome this limitation.
3. Scalability
If you ever hear a technology provider say that their software can scale to billions of images you have to be cautious. Big statements like this are misleading and do not have your best interest in mind. There are many different problems that arise with scale when it comes to face recognition within the events industry.
If you are interested in the identification scenario where the software will search a large database of faces and find the correct match there are limitations (like the ones mentioned above). Some technology vendors do not understand these limitations (or do not want you to know them). It is important to work with someone who is honest and has these insights. If your provider cannot give you a deep explanation in terms of the expected accuracy at your upcoming event, this can be a red flag. Ask as many questions as you can to the account executive and their technical team.
In addition to the database size, scalability can be an issue for large events in other ways. The amount of service needed can fluctuate from zero to beyond maximum capacity and back to zero within seconds. Most of the technology providers rent instances/servers using annual contracts to get a discount. In order to ensure availability, they throttle the number of requests that can go through. The problem is that in the event there are spikes in demand and it is not possible to smoothly adjust the number of available instances. You have to go for a high availability model. If not, the service will likely experience lots of interruptions. It is like internet service providers that put an upper limit to the bandwidth of your internet connection.
It all boils down to using a technology provider which (i) has extensive experience in the events industry and aligned interests with you; (ii) releases frequent updates and has a technology stack that is state of the art; and (iii) has a good reputation when it comes to support, reliability, privacy, security, and data handling.


In Conclusion
Event planners are eager to use the latest technology and offer a better experience to their attendees. Registration companies want to differentiate themselves and stay ahead of the curve. Facial recognition is an ideal solution for all stakeholders because it is better, faster, and more affordable than existing solutions. Event professionals can leverage its power to offer the fastest check-in solution, enhance security, extract analytics, and promote the innovative brand of their organization.
Since this is a new technology, there are some misconceptions and myths we wanted to bust. The majority of the attendees do not want to wait in line. Hence, they are more than happy to opt-in for face recognition. It is more affordable than people think and the requirements are low. Facial recognition can be extremely accurate -over 99% accurate- if you work with the right provider. Even though there are privacy regulations in some regions of the world, they do not prevent event professionals from using and benefiting from facial recognition. Instead, the regulations provide a framework that ensures all personal data is being treated properly.
There are limitless possibilities if you choose to use facial recognition and adjacent technologies. To reap all the benefits it is vital to work with a technology vendor that speaks the same language with you and has aligned interests. This will help you achieve compliance with regulations and have a better experience. It is a remarkable time to be alive and it all comes together at events.






