What’s the worst that can happen if you don’t take digital security seriously? Well, let us count the ways. The consequences of not protecting your data, managing your Zoom settings or practicing minimal security hygiene range from semi-permanently turning yourself into a cat avatar (you don’t want to be, or have to manage, that presenter) to massive fines, negative publicity and loss of trust and customers for being out of compliance with digital security rules. The FBI 2020 Internet Crime Report found a whopping $4.2 billion in losses reported last year.
Yes, cybercrime is a real threat for meeting professionals. And now that most have gotten a handle on protecting their virtual meetings, going back to physical gatherings with at least part of the program will add a whole new level of complexity.
Smart Meetings surveyed readers and experts to find out what is being done and what still needs to be done to protect our companies, our attendees and our reputations.
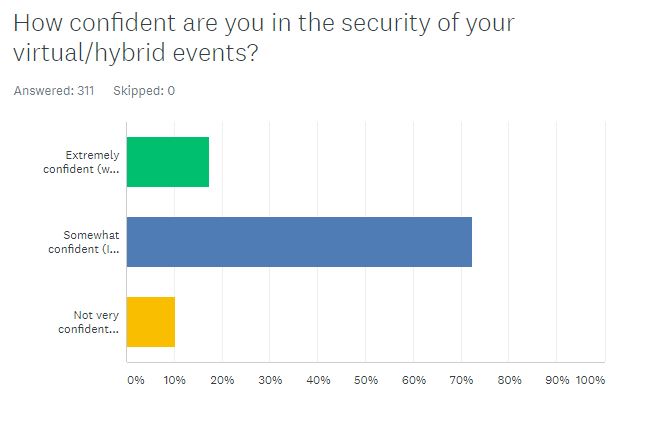
Somewhat Confident
More than 300 meeting professionals responded to our March State of Digital Security Survey and only one out of five (17 percent) said they were “extremely confident” in the security of their virtual and hybrid events (they said their events could be classified as the Fort Knox of streaming meetings). The majority (72 percent) said they were somewhat confident their platform and AV partner had checked all the boxes.
One in ten (10 percent) said they were not very confident at all: Their strategy was to keep their fingers crossed.
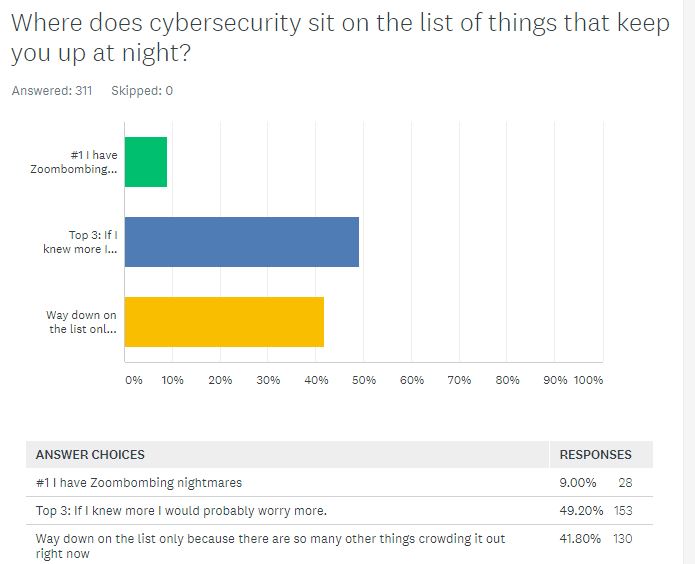
Half of those responding said digital security is in their top three concerns, noting that if they knew more, they would probably worry more. Only nine percent said Zoom bombing is the No. 1 thing keeping them up at night. The rest (41 percent) said digital protection was way down on the list, but only because so many other things are crowding it out right now.
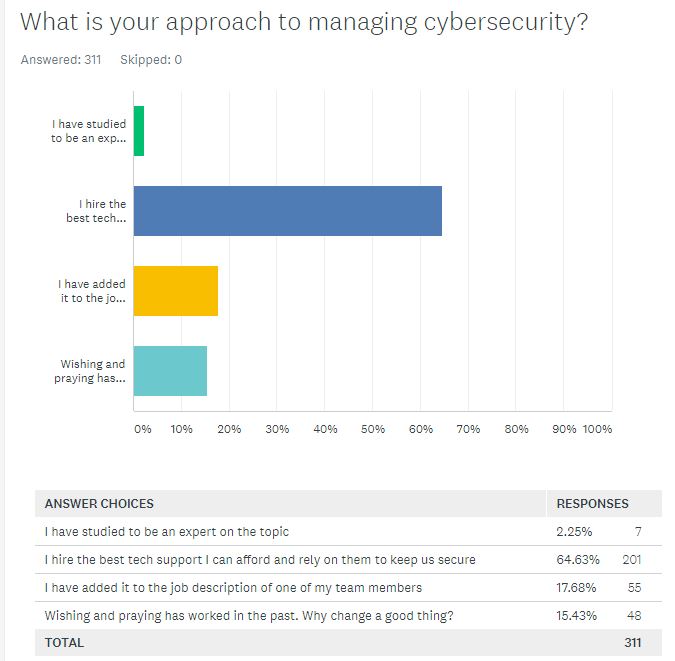
A majority (65 percent) said their approach to managing cybersecurity is to hire the best tech support they can afford and rely on them to keep the event secure. Another 18 percent had added digital security to the job description of a team member. And 15 percent admitted that wishing and praying had worked in the past, so “why change a good thing?” Only two percent said they had studied to become an expert on the topic.
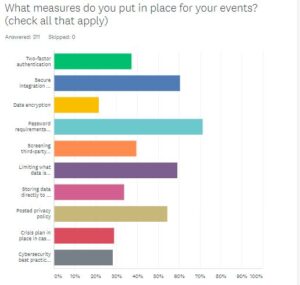 Specific steps taken to keep events safe were as numerous as the ways hackers take to break in, but the most popular were password requirements for entry (71 percent); secure integration for apps, website, registration, etc. (60 percent); and limiting what data is collected (59 percent). You can’t lose what you don’t have, correct?
Specific steps taken to keep events safe were as numerous as the ways hackers take to break in, but the most popular were password requirements for entry (71 percent); secure integration for apps, website, registration, etc. (60 percent); and limiting what data is collected (59 percent). You can’t lose what you don’t have, correct?
More than half (54 percent) posted their privacy policies; 40 percent said they screen their third-party vendors for their security practices and 37 percent use two-factor authentication.
Least common was creating a crisis plan in case of a breach (29 percent), conducting cybersecurity best practices training for the event team (28 percent) and implementing data encryption (22 percent).
Digital Risk Management: First Steps
 With so much on the line, the idea of creating a digital security program can be daunting. Rebecca Herold (pictured left), CEO of The Privacy Professor and Privacy & Security Brainiacs, who has been building information-security programs for banks and others since the ‘90s, understands that the path to a safe meeting is a process.
With so much on the line, the idea of creating a digital security program can be daunting. Rebecca Herold (pictured left), CEO of The Privacy Professor and Privacy & Security Brainiacs, who has been building information-security programs for banks and others since the ‘90s, understands that the path to a safe meeting is a process.
The list of certification acronyms after her name is lengthy, including Certified Data Privacy Solutions Engineer (CDPSE), Certified Information Systems Security Professional (CISSP), Certified Information Privacy Technologist (CIPT) and Certified Information Security Manager (CISM), but her advice about where to start is simple. The first step is to write down the policies and procedures for how people meet, pay and interact.
“Start with what information you have, where it is located, if it is secure, who is using it and who they are sharing it with,” Herold says.
 Before including a field in registration, Doreen Hollenberg (pictured left), manager of travel security and privacy with Maritz Global Events, suggests asking, “Why?” She continues: “Review what information is collected, shared or provided. Only collect what is essential to conduct the event. If it’s not needed, don’t collect it.” Then, she adds, if you do collect it, work with a provider that will encrypt it.
Before including a field in registration, Doreen Hollenberg (pictured left), manager of travel security and privacy with Maritz Global Events, suggests asking, “Why?” She continues: “Review what information is collected, shared or provided. Only collect what is essential to conduct the event. If it’s not needed, don’t collect it.” Then, she adds, if you do collect it, work with a provider that will encrypt it.
Once you have policies in place, train people to comply. This is not a one-and-done PowerPoint. Security training has to be integrated into everything you do to ensure best practices are top-of-mind—and updated as often as the bad guys find new ways to break the system.
Finally, audit how meetings are conducted. Actually, Herold doesn’t recommend using that at first, as it can put people on the defensive. Call it a review, an evaluation. “That way, the survey on whether they are complying with the policies in their new home offices and on site is seen as a teaching moment,” she says.
 Andy Jabbour, an instructor with International Association of Venue Managers’ Academy for Venue Safety & Security, recommends a block-and-tackle straight out of a playbook on Monday Night Football. “Start with everything you have been doing in the last year to ensure a safe virtual meeting. Then build on that,” he says. Jabbour is also co-founder and managing director of The Gate 15 Company and founder and senior advisor to the Faith-Based Information Sharing & Analysis Organization.
Andy Jabbour, an instructor with International Association of Venue Managers’ Academy for Venue Safety & Security, recommends a block-and-tackle straight out of a playbook on Monday Night Football. “Start with everything you have been doing in the last year to ensure a safe virtual meeting. Then build on that,” he says. Jabbour is also co-founder and managing director of The Gate 15 Company and founder and senior advisor to the Faith-Based Information Sharing & Analysis Organization.
When you get back to the meeting room, he suggests training everyone and assigning team members to monitor each area of security. In the past, you prepared for everything from fire drills to active shooters; now you have to consider threats that range from Zoom bombing to building explosions. “Just as in the NFL, you have to practice the basics,” he says.
Have a co-host ready to take over if something happens to you or your broadband during the event. And be ready to adjust on the fly by monitoring what people are doing. Be ready to take action quickly.
“Assume the worst and then enjoy the relief when it goes smoothly,” Jabbour advises.
Sometimes the little things make all the difference. “You can have the most secure app, but if you get the virtual meeting etiquette wrong, you will still be at risk of losing everything,” Herold says.
10 Questions Worth Asking
Smart Meetings’ readers suggested some pointed questions for potential tech-security vendors as we prepare to move back into the meeting space.
1. Where should we start?
2. What information should we collect and what should we specifically not collect, particularly when it comes to Covid-19 health data?
3. How secure is the cloud?
4. What PCI Security Standards are you using?
5. What, exactly, should be in a privacy policy?
6. Do you recommend virtual event insurance?
7. How do you balance encryption and convenience?
8. Is data encrypted at rest and in transit?
9. How much will it cost to protect my virtual events?
10. What have we forgotten?
Control What You Can
One of the biggest challenges for many meeting professionals about the whiplash pivot to virtual has been loss of control. At an event, we can lock the doors and go looking for stragglers in the restroom to move into the general session, but online, the variables of broadband strength, competing distractions and even temperature of the room are out of our hands. That is why you have to focus on the things you can control to protect yourself and your attendees.
 The hardware is the piece of the puzzle that’s tough to master in a WFH world, cautions Justin Maddox (pictured left), director of digital strategy at Leo Events. With internal events, planners know what devices people have and if their software is updated.
The hardware is the piece of the puzzle that’s tough to master in a WFH world, cautions Justin Maddox (pictured left), director of digital strategy at Leo Events. With internal events, planners know what devices people have and if their software is updated.
But public events could involve any kind of software or hardware or operator restrictions. “Problem-solving can be like moving boulders only to find out you are digging in a rock quarry of issues,” he says. The number of things that could go wrong when piecing together technology stacks is almost incalculable. One plug-in can distort the entire system’s security level.
Yet when setting up the streaming portion of the event, you can control a few simple things. Limit confusion by muting everyone by default. When they do have the floor to speak, ask attendees to identify themselves.
Another smart preset is to lock sharing except for those to whom you specifically grant access. Advise attendees not to open a link or file put into the chat box by anyone other than the host. It could accidentally (or on purpose) include malware that can infect home computers and spread to company networks.
You can also disable recording, but if you don’t want the video to go beyond the Zoom room, you will also have to verbally remind everyone of the no-taping policy so they don’t use another method—and hope for the best.
If you are recording, tell participants up front so they can turn off their cameras and change their names to something generic if they don’t feel comfortable being included.
Jabbour suggests color-coding documents based on how sensitive they are to help attendees understand what they can share and with whom. “But once it has been passed out, you have to assume it is public,” he warns.
Combined with invitation and password management, those steps can go a long way to defusing the threat of Zoom bombing.
Maritz’ Hollenberg calls securing the streaming environment critical. “If there is an unauthorized attendee in a meeting, they could disrupt the meeting or, more importantly, steal intellectual property,” she says, giving the example of a virtual product meeting where an unauthorized attendee captured the details, leading to a competitor making it to market before the inventors.
Like many of the respondees to our survey, she suggests relying on a vetted virtual partner if you are unsure.
Don’t Be the Weak Link

Smart Meetings event tech correspondent Brandt Krueger (pictured right) teaches a class that covers security at Event Leadership Institute (which powers Smart U), and he is passionate about protecting events because they can be a gateway for criminal activity.
When Home Depot and Target were hacked recently, it wasn’t through their own networks or servers. Home Depot was hacked via its point-of-sale credit card reader supplier, and Target was hacked through an HVAC (air conditioning and heating systems) vendor. Similarly, Russian government hackers calling themselves Cozy Bear gained access to the U.S. Treasury and Commerce departments through an update of a server at a solar company. In other words, not through the front door or back door, but rather through the side door.
“We in the event industry are suppliers to some of the largest organizations, governments and most profitable companies in the world,” Krueger says. “Think about the data we’re responsible for: names, addresses, job titles, work emails, phone numbers and, depending on your registration onboarding, even more personal information—think spouse names and home addresses.”
In-person events yield an even greater treasure-trove of data, including flight schedules, spouse and other family legal names, hotel reservations, transfer services and times, dietary preferences and so much more. That data is gold. It’s not hard to imagine a targeted email that appears to come from the limousine service with the correct dates and times listed, and a convenient “click here to confirm” button.
If you’ve used the same password for years, or “monkey123” for the password on your registration site, all that data is in danger of being exposed and used to create targeted attacks on the parent organizations. Cue the dramatic music.
Getting a password manager is Krueger’s No. 1 tip for meeting and event planners. “It’ll change your life,” he enthuses. Password managers allow you to set completely randomized passwords that are nearly impossible to crack on every site you visit. But you only have to remember one. Warning: Do your research and be wary of free password managers; otherwise, the product is you.
The next best way to protect your data is by using VPNs, or Virtual Private Networks. Basically, they are encrypted “tunnels” between the computer or device you’re working on and somewhere else. Not many years ago, VPNs gained popularity as a workaround for geographic restrictions on websites. It allowed a remote worker on the road to establish a secure connection back to the office network. It encrypts web traffic, preventing prying eyes at the coffee shop or hotel Wi-Fi from seeing what you’re up to.
Now that basically everyone is a remote worker, the bad guys are focusing their efforts on consumer-level networks, routers and Wi-Fi points that are far away from the battle-hardened intrusion detection of corporate networks.
This one may seem obvious, but almost everyone interviewed stressed the importance of password secrecy. Don’t post the password for the meeting or Wi-Fi in a place where someone might take a screenshot and share or post publicly. And don’t put the generic passwords in the email for all to see and share.
Leo’s Maddox explained the different levels of password protection. Single sign-on (SSO) allows users to access content using their existing passwords. Magic links offer unique password-less login based on email addresses. If the link matches what is behind the secure server, you are in with a single click. Multifactor authentication requires a second step to prove identity by sending a code to a phone. Some companies force this process every 3-6 months.
Most popular is the user-name/password combo with requirements for use of characters, letters, symbols and capitalization to make codebreaking more difficult. “That shares responsibility for security with participants,” he says.
Consider possible consequences when balancing convenience and safety. “That name, address and contact info needs to be as secure as your social security number. You don’t want to be that company whose CEO has to say sorry,” Maddox says, comparing the sensitivity of the registration app to the nuclear football that accompanies the president of the United States.
Jabbour says just the combination of strong passwords and two-step authorization can eliminate up to 99 percent of problems. “Criminals are looking for easy targets,” he says.
Not taking those steps “opens the door to everything from disruptions and distraction to harassment, traumatizing and compromising of sensitive information.”
Security To-dos Too Many Planners Miss

Asked about top tips, Herold points to the traps hidden in our smartphones. Tell attendees not to have other apps running or even loaded if they aren’t needed. Sometimes malicious bugs are downloaded nefariously when people answer phishing emails or take a “What Friends Character Are You” quiz, and they will send information to third parties even if email isn’t open. Practicing mindful app hygiene is particularly important if you are the host.
Another virtual faux pas that can be dangerous in streaming meetings is when the little video box reveals too much information about where the person lives or what they have of value. Herold recommends neutral backgrounds so as not to give too much away. On a related note, advise speakers to let everyone in the house know they are going to be live on-camera, so there are no accidental naked Sasquatch sightings in the background.
And everyone is now keenly aware that they need to be careful with Snapchat-style filters, so they don’t go viral as a cat or a potato (we hope).
Finally, don’t hide the privacy statement and cookie messages in small type behind the check box that gates entry to the event. Tell people how their data will be used in slides on stage, in email communication and before they log in. That will help to instill confidence.
Resources
- National Institute of Standards and Technologies (nist.gov)
- International Organization for Standardization and the International Electrotechnical Commission (iso.org)
- U.S. Department of Health & Human Services/Health Information Privacy (hhs.gov/hipaa)
- International Association of Venue Managers (iavm.org)




